Information Systems project failures may arise due to individuals and organisations failing to follow good practice. This in turn may be due to a lack of individual or collective professionalism in the IT industry.
- Find a copy of the British Computer Society Code of Conduct. Identify six professional responsibilities that a computer professional must discharge in their everyday working lives. You must present arguments explaining how the failure to fulfil each duty may well lead to IS project failure.
Any organisation processing personal data is obliged to comply with the Data Protection Act. The present Act became law in 1998.
- In YOUR OWN WORDS summarise each of the eight principles of the Data Protection Act.
The Disability Discrimination Act requires organizations to provide “reasonable” access to services and education for those with disabilities.
- How would you meet the requirements of this legislation? Focus on the various assistive technologies that are available. Identify six of these technologies and describe how they work.
Your answer should be as full as possible and approximately between 1500-2000 words in length. You must cite all sources for the information you use, i.e. list ALL references
A Data Flow Diagrams (DFD) is one type of schematic model, which can be used to reveal the processing requirements of the organisation. A DFD shows the flows of the data from users (externals) into the system, the flows of data within the system, the processing and storage of that data and the flows of information out of the system to the users.
Read the following narrative description of a process performed by academics and administration in a university:
“For the process of setting an examination paper that students will sit at the end of a semester, a Lecturer will author and submit the first draft of the exam paper to the school office. This first draft is stored in a filing cabinet and a copy sent to the Internal Moderator, who may make a number of corrections or suggestions. This internally moderated copy of the first draft is sent back to the school office with an accompanying Internal Moderator’s Form.
The school office keep a copy of this internally moderated exam paper in the filing cabinet and forward a copy to the Lecturer for the appropriate amendments to be made. Once the Lecturer has made these changes the revised exam paper is sent back to the school office, again filed away in the filing cabinet and a copy sent to the External Moderator. The External Moderator will look at this paper and send back to the school office formal comments.
At the end of the semester students will take this examination paper. Each exam paper is graded and moderated. The Lecturer then begins the process of entering the grades into the school system, which is a spreadsheet. The lecturer enters the student number and the corresponding grade into the spreadsheet. These spreadsheets are stored by the school administration staff ready for them to be presented at the Exam Board. The Exam Board, having received the spreadsheets may make any required amendments. This revised spreadsheet, containing finalised student grades, is then taken back by the school administration staff and stored.
The following day the school administration staff retrieve the spreadsheets, ready to begin the next process of entering the finalised student grades into the university system (MISIS). In this process the Student record is updated and the system presents the student with their final grade for the examination they sat”.
Using the Data Flow Diagram (DFD) notation, presented in Lecture 3, produce a DFD model of the narrative described above. You must also discuss what process modelling is and its function in the development of Information Systems. This discussion should be as full as possible and approximately 500 words. You must cite all sources for the information you use, i.e. list ALL references. These should be wide ranging, including Books, Journals and Websites.
Read the following case study, which outlines how one particular organisation assures that their IT projects are completed successfully and support the goals of the business:
Bill Morris, the Managing Director (MD) of ATP Life Assurance, talks of the successful management of IT projects: “We apply all of the analytical rigour and financial Return-On-Investment (ROI) tools against each of our IT projects as well as other business projects. The use of tools is very important, as well as risk analyses on every investment.”
The MD describes how the company monitors each IT project to measure its efficiency and effectiveness during the course of development and applies a red / yellow / green coding system to reflect the current health of a project. Senior line managers, the Managing Director and chief operating officer are all given a monthly report about the status of projects that are valued at more than £250K and those that deal with important strategic content. Also ATP Life Assurance makes use of an investment-tracking database for every IT project to monitor costs on a rolling basis. The approach gives the advantage of permitting the company’s IT and business managers to quickly determine whether a project should be accelerated, delayed or cancelled and assists the finance organisation in forecasting requirements.
Source: Adapted from O’Brien and Marakas “Avon Products and Guardian Life Insurance: Successful Management of IT Projects” in Management Information Systems, McGraw-Hill International.
- What are the key ways that ATP Life Assurances assure that their IT projects are completed successfully and support the goals of the business?
- If you were the manager of a business unit at ATP Life Assurances, identify six more things you would like to see their IT groups do to assure the success of an IT project for your business unit?
From time to time, you will be asked to submit personal information about yourself (e.g. name and email address) in order to receive or use on-line services on a website. Most organisations (business corporations and government agencies) have a privacy policy that covers the organisation’s use of personal information that they collect when you use their website.
Select three of your favourite websites and print out their privacy policies.
- List what they share in common?
- How do they differ?
- On the basis of what you have found out, from above, write your own website privacy policy.
The contemporary times have witnessed that the information and communication technology has gradually become an extremely essential part of the everyday life of all individuals and the manner in which everyone reacts with the environment.
Information systems are the most essential elements of Information and Technology that form our everyday routines and incorporate quality to the daily acts that we conduct. With each passing day new technologies are emerging and are also changing equally fast. These changes are not stagnant and are taking place all over the different countries (AntoÌn, 2003).
Various research on this field revealed that the information technology or systems project failures are primarily due to the number of risks factors attached to it. Generally the statistics provide the general failure rate that can very evidently establish for the executives of business and information technology that there exists a failure in the IS projects that is not depending on the high or low of the information technology or the information systems projects (Khosrow-Pour, 2000).
The primary objective of the research and study on this area of information technology and communications is to create awareness that can assist in reducing or resolving the failure of nay project by the use of proper and professional techniques.
There have been a number of surveys conducted with the aim to provide appropriate information with regard to the failure of the Information system and Information technology projects. Most of these surveys have been conducted by IT Cortex. The recent surveys conducted for these information system failures are The Robins-Gioia survey conducted in 2001, the Conference Board survey conducted in 2001, the KPMG Canada survey conducted in 1997, Chaos report of 1995 and The OASIG survey of 1995.
Some of the basic things that leads to information system failure that were common with regard to all the Cortex statistics are as follows:
Firstly, there was more number of Information Technology projects that failed as compared to the successful projects. Secondly, the research further revealed that the percentage of projects that were successful was a mere twenty percent and finally the rate of failure in the case of Information Technology projects are much higher than the small and medium size projects (Broy, Grünbauer and Hoare, 2007).
The failure in information technology systems can be categorized under a few headings. The first type of failure is Correspondence failure. In this sort of failure the design objectives have not been met while the system had been developed. Hence people who need an information system would never accept such an information system that did not met the guidelines that has not been met.
The second type of failure is process failure. These kinds of failure generally refers to the failure where the system has not been delivered in accordance to the time allocated for the system and the costs for the system is much more than the budget specified for the project (Wise and Debons, 1987).
The third type of failure is called the expectation failure. In this type of system failure, the failure is primarily of the system failing to meet the needs of the stakeholders and their expectations and values. Scholars in this regard has stated that expectation failure is basically the disparity that arises between what the stakeholders are expecting from them and what is being actually delivered to them.
And finally the fourth type of failure is interaction failure. The interaction failure deals with the use of the information system by the end users. It also depends on the implication as to whether the application was successful and worthy of the time given by the company. In case the system is not as much is required it would result in interaction failure.
There are certain skills that are extremely essential for the professional in an information technology department. Primarily any professional in this field is required to have the required skills and knowledge in order to undertake the work on information technology with competency. Further a professional is required to be dedicated towards the area of work and it is essential that they remain in that sphere of work. Also a professional need to declare that he or she intends to be in this profession and finally the professional while making promises to the general public or to them must keep in mind that they need to keep those promises (Fortune and Peters, 2005).
The British Computer Society can be defined as a chartered institute whose primary aim is to facilitate the information society. The objective is to promote broader economic as well as social progress by making advances in the field of information technology and science and practice (Bcs.org, 2015).
The society aims to encompass the academicians, the different industries, the government and the practitioners so that they are able to share knowledge, make improvements in the area of computer education, encourage innovative thinking, figure out the public policies and also inform the public.
This society is represented through the members and also the profession of Information Technology with regard to the different matters of significance, links with the other professional bodies. It also includes the government, the academicians, and the industries that would be able to commence and inform various debated with regard to the strategic issues in Information Technology (Bcs.org, 2015). The British Computer Society further tends to retain the relationships with a wide range of professionals and other governmental organizations.
The society is ruled by the Royal Charter that this defines the objective of the Society which is to encourage the study and use of computing and to improve the knowledge and computer education for the advantage of the general public. It is the members of the Society that makes it possible for them to propagate and promote information technology at various levels. (Refer to Appendix 2)
Some of the professional responsibilities that is given under the code of conduct of the British Computer Society are as follows:
Firstly, with regard to the public interest professional are required to have full concern for the health and well being of the public, the privacy and security of the people and the environment and also they should not discriminate on the basis of caste, creed, ethnicity, race or sex. In case, this criterion is not met with it may lead to information system failure. For instance, there are chances of information system failure when the system does not correspond to the needs of the people as had been stated by the public.
Secondly, the code of conduct specifically states that the professionals are required to take up that kind of work that is possible for them to do and that they are skilled in that particular area (bcs.org, 2015). Further they should never claim to have that sort of knowledge that they do not possess. In such cases where this code of conduct is not met, information system failure tends to increase. For instance, in case this standard is not met it might lead to interaction failure since for application to be successful it is essential that they know the work very well.
Thirdly, the code of conduct of the British Computer Society states that it is essential to promote the advantages of Information Technology and also should help to promote the different sectors in the society so as to seek the opportunities that arise in this regard. This code of conduct is aimed for the promotion of Information Technology and this is extremely essential since it forms the root of the service and hence it needs to be well promoted by the professionals for their own benefits.
Fourthly, the professional responsibilities needs to be carried out properly by the professionals with proper care and attention according to the needs and requirements of the appropriate authority and also at the same time they should be able to exercise their own professional judgment so that they are able to avoid any information system failure that might arise due to their own fault or wrongdoing. If the professionals do not carry out their work with proper care and attention the kind of failure that might arise is that there may be expectation failure where the stakeholders do not get the kind of work that they had expected from the information system.
Fifthly, the code of conduct in the British Computer Society further states that the professional are not allowed to disclose any information that is confidential to any third party for their own personal advantage or gain. However, if such act is done with the permission of the appropriate authority or such act is given under the legislation then such act is permissible. This criterion is extremely essential in any professional conduct since in case such an act might lead to the information system failure.
Finally, the code of conduct further mentions that it is the duty of the professional to accept it as a duty to sustain the reputation that the profession brings and not to indulge in any such act that might bring disrepute to the profession. It is essential that the professional rules and regulations are improved while developing or using the technology. It is extremely essential that the professionals conduct their work properly so as to bring in less information system failures.
The Data Protection Act 1998 (DPA) of the United Kingdom including Great Britain and Northern Ireland is an Act of Parliament that deals with the process of data on the living people. It is a primary legislation that deals with the protection of data in the countries of United Kingdom. Primarily the Data Protection Act of 1998 comprises of eight important principles (Rowe, 2000). Firstly, personal data needs to be processed properly and legally until and unless one of the conditions given in Schedule 2 is considered and in cases where the personal data is sensitive one of the conditions of Schedule 3 should be maintained. The personal data that is obtained shall be only for the specific lawful purposes and such data should not be processed in any other way that is not compatible with those specified purposes (Carey, 1998).
Further the act states that the personal data needs to be enough and appropriate with regard to the purposes for which it has been processed. The personal should also be accurate and regularly updated (Oppenheim, 2000). The data that has been processed for any purpose should not be kept longer than it is required for that particular purpose (Mullock and Leigh-Pollitt, 2000).
For the rights of the people such data needs to be processed according to the rights given to data subjects. Proper technical measures needs to be taken against the illegal processing of data and any accidental loss or damage of the data. And finally personal data cannot be transferred outside the territory of European Economic Area (Wiewiorka, 2002).
The Disability Discrimination Act of 1995 was a civil rights law that is prevalent presently in Northern Ireland (Vellani, 2013). It regulates any kind of discrimination against the people relating to education, employment, transportation etc.
The act provides a number of such technologies that would be useful for the disabled people. For instance, the act provides that information be displayed on the computer screen for the disabled people, or information be provide on the computer disc or email for the disabled people who are visually impaired (Doyle, 2008). Further disabled should be given job information that is accessible by such person like computer disc or Braille. It provides for adjustments made for taking tests by the disabled by giving them computer with voice recognition software for the purpose (Wright and Conley, 2011). Also trade organization can make probable adjustments by giving the disabled online applications for their use.
Process modelling can be considered as an act of representing the relationship among all activities of a business (Cutshall, 2007).Process modelling is done to analyze the business activities. Karn, (2013) stated that process modelling can be used for finding the drawbacks in existing business process. It indicates that process modelling can improve the efficiency of business activities.
The process in business is composed of more than one sub processes. As the processes mentioned in dataflow diagram can be divided into several subtasks, the data flow diagram shows hierarchical nature. However the higher level processes can be considered as parent process. Gurses and Diaz (2013) stated that incoming and outgoing flow of data requires being shown while describing hierarchical data flow diagram.
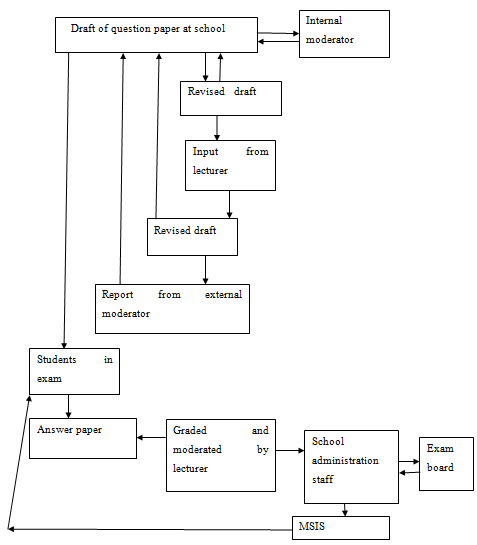
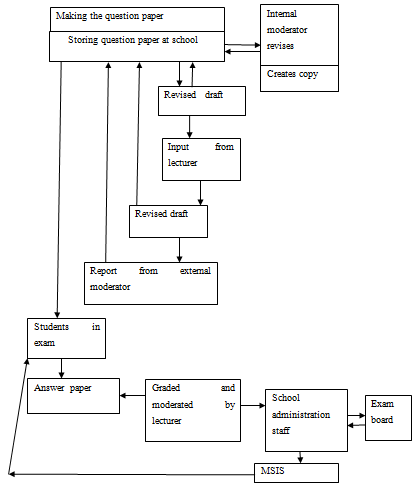
Figure 2: Level 2 DFD
DFDs are used for showing the relationship among various parts of a process or entity. ERDs are used for showing the relationship among different entities within a process. DFDs are used for describing a system in detail (Cutshall, 2007). However ERDs are also used for analysing the nature of relationships among various processes.
As stated by Gurses and Diaz, (2013) critical success factors of the project are some specific areas which determine whether the project will be successfully completed or not. Cutshall (2007) opined that critical success factors can be considered as parameters for measuring performance of a project The analysis indicates that critical success factors can be considered as those areas which require being focused during execution of a project. Lack of focus in the areas of critical success factor may restrict an organization from getting desired result.
In Avon Insurance the management uses some tools for enhancing the effectiveness of IT projects. Analysis of the case study indicates that the organization uses red/yellow/green coding system to assess the current status of a project. The management also uses reporting systems to monitor the progress in project. As a project is executed by different teams within an organization, collaboration among the teams is important to complete the tasks successfully. In Avon the senior line managers managing director and chief operating officer all monitor the progress in project. Collaboration among the senior managers also enables the teams for co-operating with each other. The members of senior management team receives reports on the project status and they develop future strategies for completing the project on basis of the report. Top management of Avon Insurance focuses on completing the project within budget. The organization uses investment tracking database for completing the project in cost effective manner.
Use of Colour coding system: Gurses and Diaz, (2013)stated that the use of colour coding system not only provides senior management with the information regarding condition of the tasks, it is also beneficial to avoid issues. Karn, (2013) opined that use of red/yellow/green colour coding system enables the project team to understand whether any help from management is required or not. The coding system uses three colours. The colour red indicates that the project team needs external help in order to meet the objectives. Menachemi and Singh, (2012) stated that the red colour indicates that the project team has faced serious issues while executing their tasks. Red colour also indicates that the issues faced by project team cannot be solved by them. The colour yellow in coding system indicates that the project may not be completed within time or budget (Menachemi and Singh, 2012). The project can be executed efficiently due to use of colour coding system (Qatawneh, 2012). According to Aseeva et al.,( 2012) use of colour coding system is not only beneficial for project team, it is also effective for management of the organisation also. Ardagna (2012) stated that use of colour coding system also provides the management with information regarding their action at different phases of project. If the status indicates red colour, the management require taking immediate actions to solve the issues faced by project team (Yousef Obeidat, 2012). Use of yellow colour indicates chances of delay in project execution. The management require informing the sponsors about delay or cost overrun. Green status in the coding system indicates that management may not require taking any action. As the management of Avon uses colour coding system, the managers can predict whether the execution of project will be interrupted due to presence of issues or not. Analysis on the colour coding system also indicates that use of it enables Avon management to take immediate actions in response of an issue.
Reporting senior line manager: Members of the project team in Avon report regularly to the senior line manager regarding status of the project. VojtaÌsÌŒ (2013) stated that the line managers play vital roles in panning and organizing the tasks in project. According to Vie (2015) line manager is also responsible for ensuring that none of the resources are being wasted while executing the project. It indicates reporting to line manager ensures that any incidence regarding delay in project or additional budget requirement can be predicted in advance. Rahman, (2012) opined that the line managers are responsible for maintaining collaboration among members of the project team. Reporting the status of project to the senior line manager enables Avon management to assess the performance of teams. Reports to the senior line manager also enable the management to identify whether the project team requires any training. As the project team of Avon provides the line manager with information on progress in work , the management becomes able to understand the need of any resources for timely completion of the project. As the requirements of resources are identified, projects in Avon can be executed uninterruptedly.
Reporting managing director: Reporting to the managing director is effective for assessing whether the project will be able to meet objectives of an organisation (Qatawneh, 2012). The managing directors also analyse the reports to evaluate the process of implementing company policies into project management techniques. The managing director also evaluates the performance of project team. Avon Insurance conducts different IT projects to increase efficiency of the business units. Reports to managing director enables the organisation to identify whether the goals of company will be achieved after completion of the project.
Reporting Chief operational officer: According to Peffers et al.,(2012) reporting to Chief Operating Officer enables the management to identify the requirement of bringing changes in operational activities of the project team. Although the COOs deal with evaluating monitoring the operational activities of a team, reporting to the operational officer can be effective to decide the future strategies of project team. The discussion on the role of COO in project management indicates that reporting to COO in Avon enables the project team to understand need of changing existing strategies. As the operational activities are changed regularly, efficiency of team increases in Avon.
Using monthly reports for strategy development: As the Avon management undertakes most of the IT projects for improving business performances, the management requires changing strategies regularly. Assessing the project activities is effective to predict whether the project will be able to meet business goals. However different members of the top management team are responsible for developing different business strategies. Reporting to the line manager enables the management to develop strategies regarding the requirement of additional resources. However, it is also effective to evaluate the functioning of project team. Reporting to the managing director of Avon enables the project team to implement the policies of an organisation into project activities. The strategies related with change management in project are developed by the chief operating officer in Avon. As the project team reports to the COO of Avon regularly, the team understands whether their activities are meeting organisational objectives or not.
Using investment tracking database: Analysis of the case study indicates that the management of Avon uses investment tracking database to assess the performance of projects. Nakahara and Sasaki (2013) stated that the effectiveness of a project depends on the amount of ROI (return on investment). As the management uses investment tracking database in the organisation, cost effectiveness of the project can be assessed easily.
Although the existing project management system in Avon is effective to execute the activities effectively, the management can implement some additional practices into their current project management techniques. Menachemi and Singh (2012) opined that implementation of advanced project management system does not ensure that all the projects will be completed successfully. (sd) states that each IT project is unique. These projects cannot be completed successfully due to various reasons. The Avon management can analyse the causes of failure of unsuccessful projects to improve their performance. The management can also implement professional codes to assess the performance of each employee who are involved with the project.
Luo (2012) stated that online privacy can be considered as the security of personal data which are shared using internet. As the use of internet activities increased significantly , the number of issues related with privacy loss is increasing among the users. Often the internet users require sharing their personal information such as name, address contact number or bank details to conduct different activities over internet. However the platforms where these sensitive information are being share requires ensuring that confidentiality of such information will be maintained. In most of the cases e-commerce platforms or social networking sites uses some rules to ensure that the information regarding a person are not disclosed. Krishnamurthy (2013) opined that increasing number of internet crimes often lead to loss of privacy. Often the e-commerce and social networking sites show interest to store the personal information about customers. These sites may store the details regarding products or services. However, these platforms require informing their customers about the information which will be stored by these platforms. Luo (2012)stated that publishing or sharing personal information without the consent of user may lead to breach of privacy policies.
Although privacy policies in different websites are used for keeping the data secured, some differences are observed among the privacy policies of government, private and NGO websites. Karn, (2013) stated that purpose of data collection by a website varies according to the nature of organisation. Differences in purpose of data collection lead to generation of different privacy policies (Gurses and Diaz, 2013). However Fuchs et al., (2012) stated that presence of some common policies is also observed among different websites. In this assignment, privacy policies of UK government website, Tesco website and international HIV/AIDS Alliance website are analysed to identify the similarities and differences among them.
The website of UK government collects data regarding the IP address, name and e-mail address about the visitors for monitoring how visitors use websites. Data on the visitors are also collected for responding to the queries. Tesco, UK based retailer, uses cookies to collect data on the internet browsing activities of visitors. However, the organisation also provides information to the visitors on purpose of collecting information. However, information collected on the visitors is used by Tesco website not only for improving the functionality but also for personalizing the site. The information for managing cookies is also provided in the privacy policies of Tesco. Alliance an international NGO requires collecting data for serving people. However cookies are also used in the website of alliance. (Refer to Appendix)
URLs of the selected websites are as follows:
UK Government website privacy policies:
https://www.gov.uk/help/privacy-policy
Privacy policies for TESCO website:
https://www.tesco.com/help/privacy-and-cookies/
Privacy Policies for Alliance Website:
https://www.aidsalliance.org/about
Discussion on the privacy policies of UK government, Tesco and Alliance website indicates that all these websites use some common privacy policies.
|
Factors |
UK Government website |
Tesco Website |
Alliance Website |
|
Informing visitors about data collection |
Informs |
Informs |
Informs |
|
Informing about the type of data collection |
Informs |
Informs |
Informs |
|
Stating the purpose of collecting data |
Informs |
Informs |
Informs |
|
Information regarding the process of data collection |
Informs |
Informs |
Informs |
|
Information regarding the process of data sharing |
Informs |
Informs |
Informs |
Table 1: Similarities among the privacy policies of three websites
Analysis on the privacy policies of three websites indicates that all the websites inform visitors about the data collection. Although the websites collect data for different purposes, visitors are also provided with information regarding the purpose of collecting. The decision of users for visiting a website can be influenced by data collection policies of that website (Faculty.stedwards.edu, 2015). It indicates that providing the information on data collection policies is important to maintain privacy of visitors. Foster (2012) opined that informing the visitors about type of collected data enables the websites to maintain transparency of the process. Analysis on the privacy polices of three websites indicates that all the organization focus on using transparent data collection process. According to Cutshall (2007) privacy policies of the websites require containing information on the policies for sharing data. Discussion on the privacy policies of UK Government website, Tesco Website and Alliance website indicates that visitors of all these websites are informed whether their personal data will be shared or not.
As UK government website, Tesco website and Alliance website serves the visitors for different purpose, privacy policies of these websites are also different.
|
Factors |
UK Government website |
Tesco Website |
Alliance Website |
|
Use of cookies |
Does not use cookies |
Uses Cookies |
Uses Cookies |
|
Information on the policies of managing cookies |
NA |
Provides information for managing cookies |
Does not provide any such information |
|
Information on storage of data |
Provides information on data storage process |
Does not provide any such information |
Does not provide any such information |
|
Guarantee on data security |
Ensures that individuals cannot be identified from collected data |
Ensures that data will be secured |
Does not provide any guarantee for maintaining security of data during transmission |
Table 2: Differences between privacy policies among three websites
Discussion on the privacy policies of the three selected website reflects some major differences. Tesco being a commercial website uses cookies for tracking the internet activities of a visitor. However the website also contains information so that the visitors can manage cookies by changing browser settings. Alliance website also uses cookies but the visitors are not provided with any information regarding the management of cookies. Website of UK government is not used for conducting any marketing activities. Thus the website does not use cookies for tracking activities in the browser of a visitor. Website of UK government contains full information on data storage on server. In case of Tesco website, security of data is ensured and the users can restrict organisation from collecting personal data. However the website of Alliance does not provide any guarantee on data security during transmission. However the organisation ensures that full effort will be given to maintain security of stored data.
Colantonio et al., (2012) opined that difference in the functionality of websites also leads to development of different privacy policies. UK Government does not require conducting any marketing activities. Thus the website does not require using cookies for tracking the visitors’ activities. Tesco uses cookies for conducting marketing activities while Alliance uses it to understand the requirements of their stakeholders in more efficient manner. As the website of Tesco is used for conducting commercial activities, visitors may not allow the organisation for using their information. Alliance operates in different countries and availability of advanced technology is not equal in those countries. Alliance does not provide any guarantee of maintaining data security during transmission. Data on the visitors of UK government website is required for conducting limited activities .Thus the chances of data security loss reduces. Secrecy of data is guaranteed UK government website.
The website developed by our group will use cookies for collecting data about the visitors. However, visitors of the website will be informed about the data collection. Privacy policy of our website will also include information regarding type of collected data and purpose of collecting data. Security of the data collected in groups’ website will be maintained. The data will be protected according to the Data Protection Act. Loss of data security can result ethical issues. However such issues will be resolved by applying Ethical Normative principles. Colantonio et al., (2012) stated that use of ethical normative principles reduces the negative effects of ethical problems.
Aseeva et al.,(2012)opined that cookies are text files which are used for tracking the browsing activities of a internet user. Content of the cookies can be read only by server. Generally the cookies contain information on the sites. According to Ardagna (2012) each cookie can be identified uniquely. However cookies can be deleted from computers or mobiles.
The study above provides a brief outlook of the laws governing information technology in the United Kingdom. It gives knowledge of the methods to tackle information system failures and the framework of the information laws that are necessary to regulate the laws of the country. Analysis on the process modelling indicates that use of process modelling is effective to understand the relationships between all processes within a business. Use of DFD provides detailed information regarding the data flow among processes whereas use of ERD provides information regarding the interactions among various processes. Discussion on the critical success factors of projects indicates those areas which require being focused during execution of a project. Last section of the assignment deals with online privacy policies. The discussion on online privacy polices indicates that the number of issues related with privacy loss is increasing among internet users. However the website developers can use different privacy policies according to the functionality of website.
AntoÌn, P. (2003). Finding and fixing vulnerabilities in information systems. Santa Monica, CA: Rand.
Ardagna, C. (2012). Business system management and engineering. Berlin: Springer.
Aseeva, N., Babkin, E. and Kozyrev, O. (2012). Perspectives in business informatics research. Berlin: Springer.
bcs.org, (2015). BCS, The Chartered Institute For It Trustee Board Regulations - Schedule 3 Code Of Conduct For Bcs Members. [online] Available at: https://www.bcs.org/upload/pdf/conduct.pdf [Accessed 1 Apr. 2015].
Bcs.org, (2015). BCS - The Chartered Institute for IT. [online] Available at: https://www.bcs.org/ [Accessed 29 Mar. 2015].
Broy, M., Grünbauer, J. and Hoare, C. (2007). Software system reliability and security. Amsterdam: IOS Press.
Carey, P. (1998). Blackstone's guide to the Data Protection Act 1998. London: Blackstone Press.
Colantonio, A., Di Pietro, R. and Ocello, A. (2012). Role mining in business. Singapore: World Scientific.
Cutshall, R. (2007). Computer Privacy Annoyances — How to Avoid the Most Annoying Invasions of Your Personal and Online Privacy. Journal of Information Privacy and Security, 3(4), pp.55-56.
Doyle, B. (2008). Disability discrimination. Bristol: Jordans.
Faculty.stedwards.edu, (2015). Principles of Normative Ethics. [online] Available at: https://faculty.stedwards.edu/ursery/norm.htm [Accessed 1 Apr. 2015].
Fortune, J. and Peters, G. (2005). Information systems. Hoboken, NJ: Wiley.
Foster, A. (2012). Let's integrate - information services, content, technologies and collaboration: The Business Information Survey 2012. Business Information Review, 29(1), pp.9-28.
Fuchs, M., Ricci, F. and Cantoni, L. (2012). Information and communication technologies in tourism 2012. Vienna: SpringerWienNewYork.
Gov.uk, (2015). Data protection - GOV.UK. [online] Available at: https://www.gov.uk/data-protection/the-data-protection-act [Accessed 1 Apr. 2015].
Gov.uk, (2015). Data protection - GOV.UK. [online] Available at: https://www.gov.uk/data-protection/the-data-protection-act [Accessed 1 Apr. 2015].
Gov.uk, (2015). Privacy policy - GOV.UK. [online] Available at: https://www.gov.uk/help/privacy-policy [Accessed 1 Apr. 2015].
Gurses, S. and Diaz, C. (2013). Two tales of privacy in online social networks. IEEE Secur. Privacy, 11(3), pp.29-37.
International HIV/AIDS Alliance., (2015). Privacy and cookies. [online] Available at: https://www.aidsalliance.org/privacy-policy [Accessed 1 Apr. 2015].
Karn, B. (2013). Fuzzy Logic Based Information Retrieval System. Saarbrücken: LAP LAMBERT Academic Publishing.
Khosrow-Pour, M. (2000). Organizational achievement and failure in information technology management. Hershey, Pa.: Idea Group Pub.
Krishnamurthy, B. (2013). Privacy and online social networks: can colorless green ideas sleep furiously?. IEEE Secur. Privacy, 11(3), pp.14-20.
Luo, J. (2012). Soft computing in information communication technology. Berlin: Springer.
Menachemi, N. and Singh, S. (2012). Health information technology in the international context. Bingley, U.K.: Emerald.
Mullock, J. and Leigh-Pollitt, P. (2000). The 1998 Data Protection Act. London: Stationery Office.
Nakahara, M. and Sasaki, Y. (2013). Quantum information and quantum computing. Singapore: World Scientific.
Nidirect.gov.uk, (2015). The Disability Discrimination Act (DDA) | nidirect. [online] Available at: https://www.nidirect.gov.uk/the-disability-discrimination-act-dda [Accessed 1 Apr. 2015].
Oppenheim, C. (2000). The Data Protection Act, 1998. [London]: SCONUL.
Peffers, K., Rothenberger, M. and Kuechler, W. (2012). Design science research in information systems. Berlin: Springer.
Qatawneh, A. (2012). The Effect of Electronic Commerce on the Accounting Information System of Jordanian Banks. International Business Research, 5(5).
Rahman, H. (2012). Knowledge and technologies in innovative information systems. Berlin: Springer.
Rowe, H. (2000). Tolley's Data Protection Act 1998. Croydon, Surrey, England: Tolley.
Tesco.com, (2015). Privacy and Cookies Policy - Tesco.com. [online] Available at: https://www.tesco.com/help/privacy-and-cookies/ [Accessed 1 Apr. 2015].
Vellani, F. (2013). Understanding Disability Discrimination Law through Geography. Farnham: Ashgate Pub.
Vie, D. (2015). Understanding Data Flow Diagrams. [online] Available at: https://ratandon.mysite.syr.edu/cis453/notes/DFD_over_Flowcharts.pdf [Accessed 1 Apr. 2015].
VojtaÌÂsÌŒ, P. (2013). Information modelling and knowledge bases XXIV. Amsterdam: IOS Press.
Wiewiorka, E. (2002). Data Protection Act 1998. Edinburgh: W. Green/Sweet & Maxwell.
Wise, J. and Debons, A. (1987). Information systems. Berlin: Springer Verlag.
Wright, T. and Conley, H. (2011). Gower handbook of discrimination at work. Farnham, Surrey, England: Gower Pub.
Yousef Obeidat, B. (2012). The relationship between Innovation diffusion and human resource information system (HRIS). Perspectives of Innovations, Economics and Business, pp.41-58.
To export a reference to this article please select a referencing stye below:
My Assignment Help. (2016). Law And Information Essay. Retrieved from https://myassignmenthelp.com/free-samples/law-and-information.
"Law And Information Essay." My Assignment Help, 2016, https://myassignmenthelp.com/free-samples/law-and-information.
My Assignment Help (2016) Law And Information Essay [Online]. Available from: https://myassignmenthelp.com/free-samples/law-and-information
[Accessed 19 August 2024].
My Assignment Help. 'Law And Information Essay' (My Assignment Help, 2016) <https://myassignmenthelp.com/free-samples/law-and-information> accessed 19 August 2024.
My Assignment Help. Law And Information Essay [Internet]. My Assignment Help. 2016 [cited 19 August 2024]. Available from: https://myassignmenthelp.com/free-samples/law-and-information.
